Playing with OS module in Online Python Interpreters
Online Python Interpreters
There are lots of Online python interpreters available freely on Internet. These allows us to learn, run and test our codes written in python. Python is an interpreted, object-oriented high-level programming language with dynamic semantics. It is user-friendly, easy and open-source which makes it one of the most popular programming language globally. You can learn more about python on their official website https://www.python.org/
Some of the online Python Interpreters are listed below :
- Python.org
- Replit Online Python Interpreter
- OnlineGDB Python Interpreter
- SymPy Live
- Python Interpreter Online
- Online Python
- Programiz Online Python Interpreter
- And many more which you can easily find on Internet.
OS module in Python
The OS module in python allows us to access operating system dependent functionality within the python itself. You can learn more about OS module here.
we import the OS Module in python by just adding :
import os
in our program on the top. Some of the basic parameters of OS modules are : getcwd(), system(), chdir(), mkdir(), name, etc.
OS.NAME & OS.SYSTEM() in OS Module
Now starting with the topic of accessing the system (Bot server of Online Interpreter), we will be needing to know about the system itself. I assume the viewer have somewhat knowledge about the terminal. For this, we type :
import osprint(os.name)
The name of the operating system dependent module imported. The following names have currently been registered: 'posix', 'nt' & 'java'
For online interpreters(I'm using replit.com), it probably shows 'posix' because almost all server are linux-based Server OS.
Now we know which type of OS are we working with, so moving forward;
Let's revise our linux terminal knowledge because we will now be using the system() parameter.
The system() allows us to execute a command (as a string variable) in a subshell.
This is implemented by calling the Standard C function system(), and has the same limitations. To implement the system() :
import osos.system("your command")# the string inside os.system("") gets executed in the subshell
For example :
import osos.system("pwd")
Now let's get to work!
Writing the actual code and troubleshooting some errors
We don't want to run the program each time we execute a command. So to fix that lets introduce a variable called "command_in" where we store our command string and add an infinite while loop. To do so, we do:
import oswhile 1:command_in = input(str("Enter your command : "))os.system(command_in)
This shall work pretty fine. Let's try out some commands like :
pwd
clear
ls
cd ..
You can find other linux commands here : https://www.tecmint.com/linux-commands-cheat-sheet/
but wait! why aren't we allowed to change the directory?
Entering "cd .." doesn't seem to work. Well it's one of the limitations there, but don't worry. We still have ways to fix it. This is where out chdir() parameter comes in handy!
but how are we going to implement it?
for that let's add if, elif & else functionality.
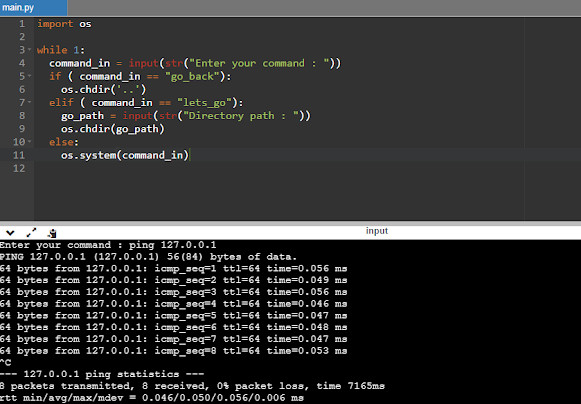
import oswhile 1:command_in = input(str("Enter your command : "))if ( command_in == "go_back"):os.chdir('..')elif ( command_in == "lets_go"):go_path = input(str("Directory path : "))os.chdir(go_path)else:os.system(command_in)
let's run it now! First let's check if we can go back:
we are able to go back now.
Let's try to enter other directory now:
you can try other things too! like creating folders, deleting it, renaming it, and even creating your own file!
Yes you saw that right! We can create file too!
Yes you saw that right! We can create file too!
In this example we are going to use VIM as our text editor, not only vim, even gcc is available!
let's create a simple C program!
let's create a simple C program!
vim <yourfilename>.c
example :
vim hello.c
and press enter.
For an individual who has never used or has never been familiar with VIM, editing part is tricky.
To add code or insert characters, we must first go to insert mode, by pressing "i"
on pressing "i", on the bottom left you should see "-- INSERT --" which means you are in insert mode.
now let's start coding!
For that we need to exit the insert mode, by pressing "esc" key.
Soon after that "-- INSERT --" prompt on the bottom disappears, which indicates we escaped the insert mode.
Soon after that "-- INSERT --" prompt on the bottom disappears, which indicates we escaped the insert mode.
Now in order to save the file and exit.
we type:
:wq
where :w tells VIM to save and :q tells it to quit, Combined, we get :wq
which saves and quit the program.
now that the program is saved, let's compile and run the program!
To do so, we have GCC a program to compile C/C++
we type :
we type :
gcc <yourfilename>.c -o "<newName>.out"
example :
gcc hello.c -o hello.out
the parameter "-o" sets the new path and new file name for compiled program
if the gcc passes without any prompt or any error, your program was successfully compiled, but if there's error, re-edit the program by VIM again.
My program worked properly so it didn't show any error.
Let's check the files now :
There's my compiled file "hello.out"
let's run it by typing :
./hello.out
if your file doesn't get executed like this, run : chmod +x <filename>
and try again.
I hope you guys learnt something new today! Peace!
Conclusion
You can go and create your own subshell in any online python interpreter and try different linux commands. Some of the interpreters even allows you to access "ifconfig" commands, and access the network, which can help us doing some nasty things like network attacks, server attacks, ddos, etc. but i suggest you not to go on the darker side.
Feel free to modify the codes as you like. Share it to your friends and family, and please let me know if you have any queries. Happy Coding!!